Challenge Exploration
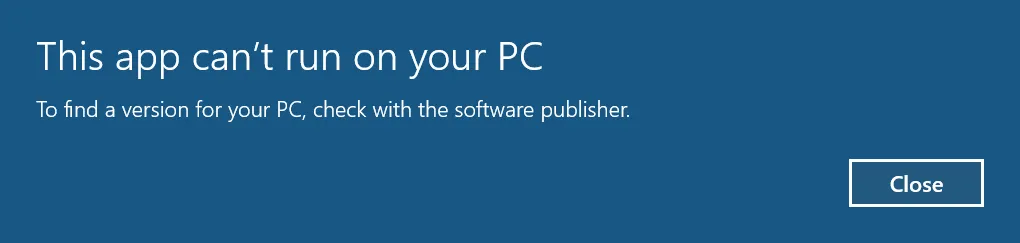
The challenge gives us a Windows executable but it can’t be executed!
I tried running the program through Terminal as well and Windows told me that this is a 16-bit executable in a random popup. Is that true? If that’s the case, trying to get the binary running would be difficult so I decided to load this file in IDA to see what it does.
Actually It’s Corrupted
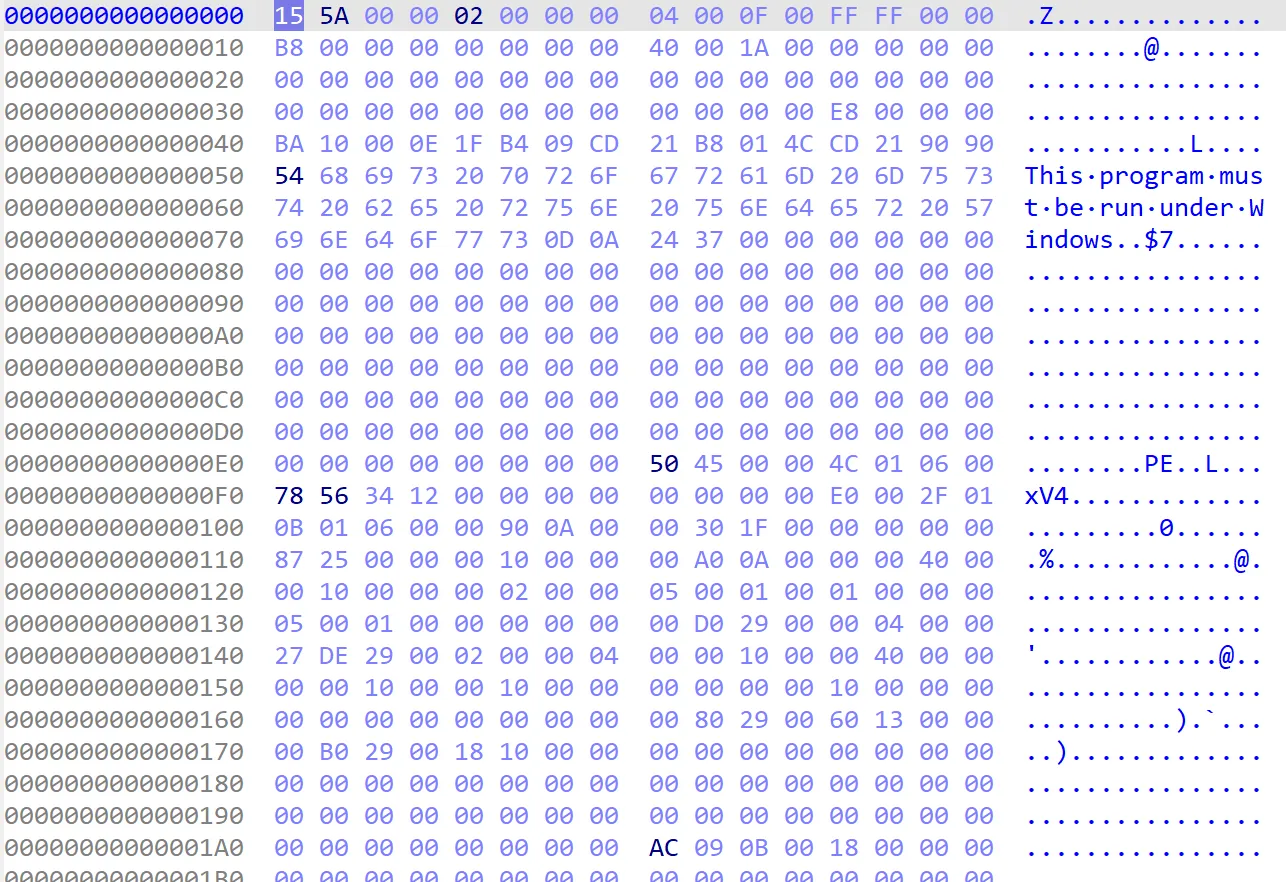
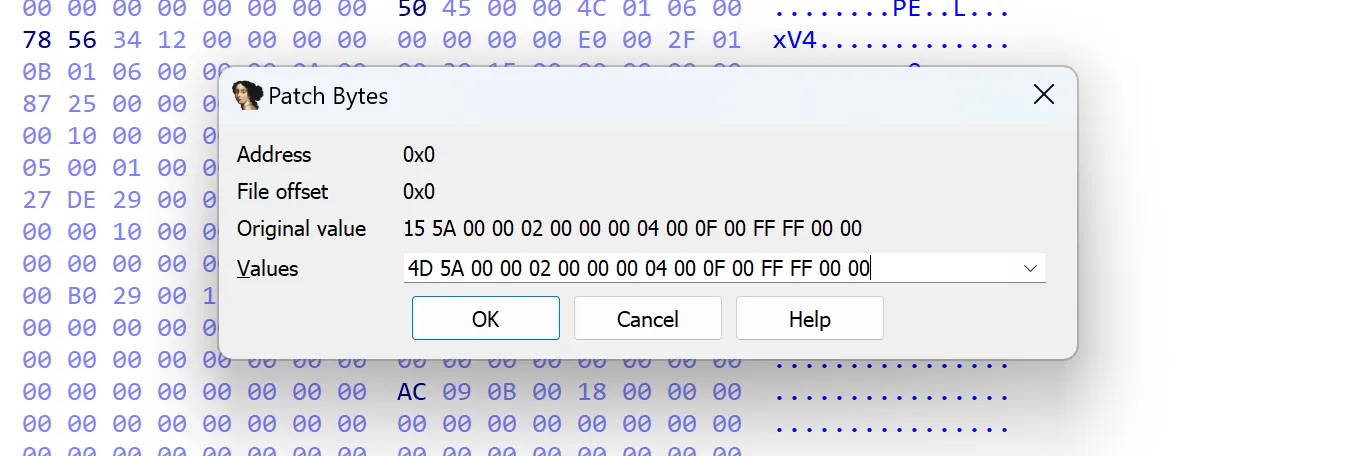
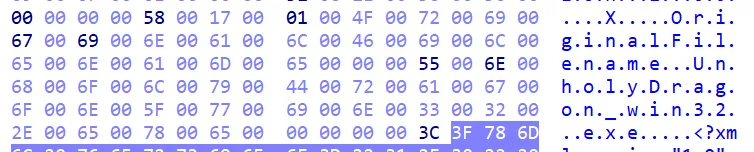
After poking around a bit inside IDA, I still couldn’t get an idea what this program was supposed to do! At one point I switched to Hex View and noticed that the magic number of the PE executable is corrupted. The first byte of the header was 0x15 instead of 0x4D.
So I’ll just patch the byte to 0x4D.
Okay, that works as the binary changed its icon!
Lots And Lots Of Clones
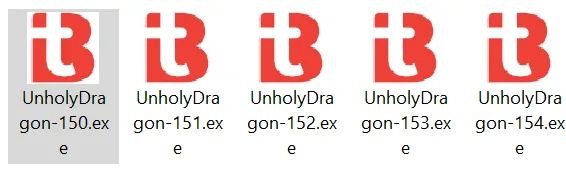
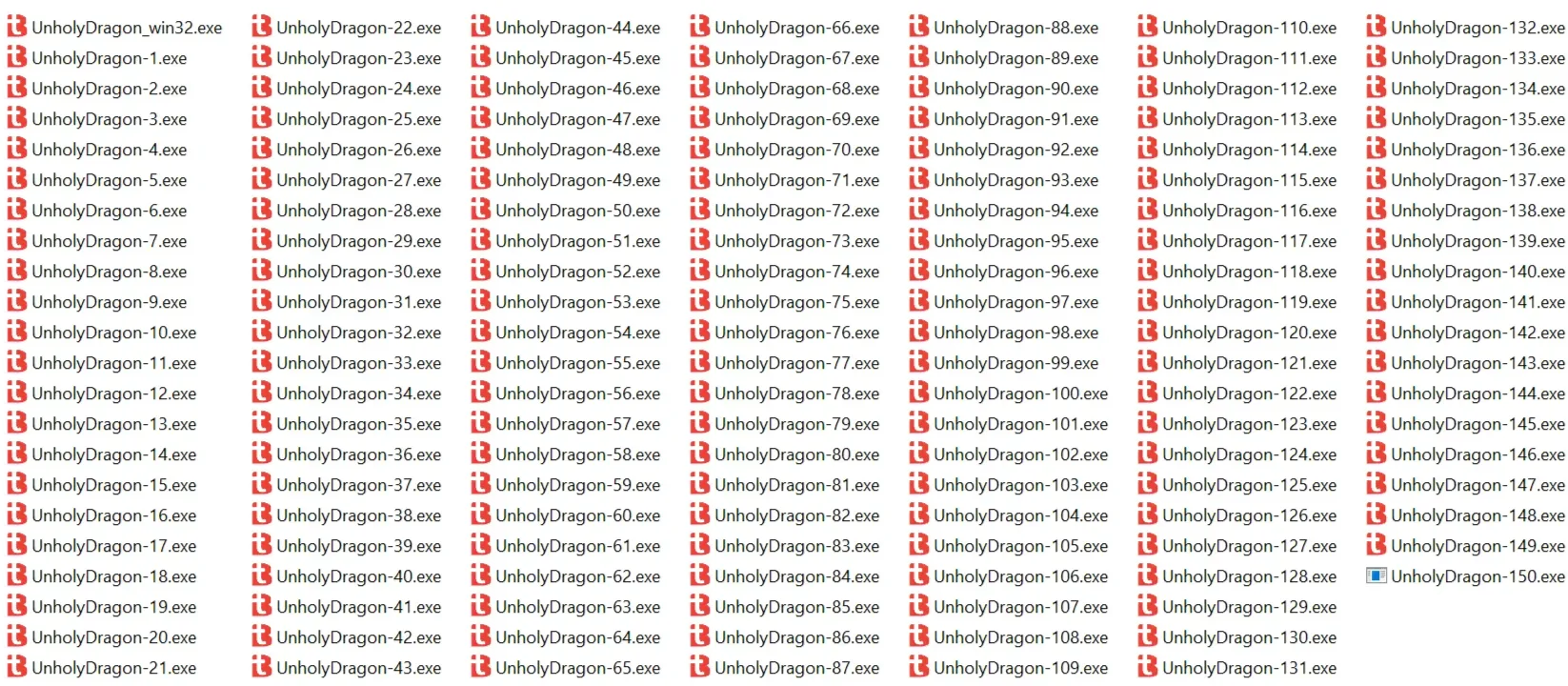
I clicked on the patched executable and it created 4 more files. But nothing happens next.
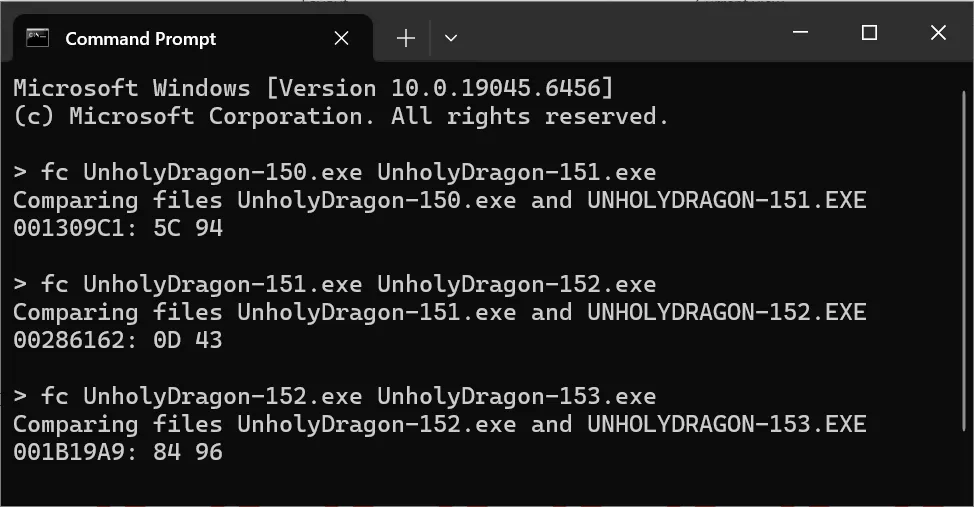
Maybe diff-ing the executable would give some hints. I opened up Terminal to use the fc command, and its output shows that each pair of .exe files differs by exactly one byte.
At this point I guess the executable just clones itself and changes exactly one byte of the new file upon launching. Wait, the original binary has the first byte of the PE header changed. Maybe it is a self-modified clone as well. So if we have UnholyDragon-150.exe, we should have UnholyDragon-149.exe, right?
Then I renamed it to UnholyDragon-149.exe. The program instantly created UnholyDragon-150.exe with a corrupted header. I repeated the patching process above and launched the -150.exe executable again, saw the cloning, but nothing happens next.
I started digging into the hex and saw something in the Version Info Resource section of the PE. Looking at the Original Filename metadata, the PE might have been built as UnholyDragon_win32.exe.
I instantly renamed UnholyDragon-150.exe to UnholyDragon_win32.exe. I got another 150 clones with a bunch of empty windows opened. As I expected, the newly-created UnholyDragon-150.exe is corrupted.
I was too lazy to patch it again this time. Knowing that the one byte that changed was the header’s magic number and patching it would create a binary identical to UnholyDragon-149.exe. So I just delete the corrupted PE, duplicate UnholyDragon-149.exe and rename it to UnholyDragon-150.exe.
I clicked on UnholyDragon-150.exe, hoping to create the final 4 clones (I was expecting to see the flag hidden somewhere in UnholyDragon-154.exe after all of these 154 times of byte changes). Then the 4 new clones launched, and I saw the flag in one of the window!
Maybe this window belongs to UnholyDragon-154.exe I guess…
dr4g0n_d3n1al_of_s3rv1ce@flare-on.com Thoughts
I thought this is kind of like a guess-what-the-author-wants-you-to-do challenge. Most of the time had no idea what I was doing and just guessed my way through it. There wasn’t any actual reversing involved either.
Later I discovered that you can actually rename the binary to any name, except UnholyDragon-1.exe though UnholyDragon-154.exe, to create the other 150 clones.